Most modern crypto products such as exchanges and wallets have user interfaces that take the long strings of randomly looking data away from our eyes and replace it with human-readable text whether its mnemonic phrases or names of the wallets. However, if you ever read about the inner design of cryptocurrencies you know that the blockchain technologies are unthinkable without encrypted data expressed in hash strings.
Hashing is one of the fundamental components of any blockchain-based product. Hashing secures the blockchain data and serves as a signature or an identifier for the pieces of information stored on-chain. Hashes are created with the use of sophisticated math formulas that ensure that all the attempts to retrieve the original input through analyzing the hash will fail. The article explains what is blockchain and what role do hash functions play in keeping it safe.
What Is Blockchain Technology?
Blockchain technology was introduced with the emergence of the first cryptocurrency, Bitcoin. Blockchain is a digital data ledger distributed among numerous nodes (computers).
The data stored on the blockchain is immutable. None of the nodes has control to overwrite, change, or delete the data on the blockchain. As new transactions take place the data about them is validated and recorded in this ledger. Blockchain-based networks are trustless as they are fully automated and have various ways to prevent spam attacks and frauds. On top of decentralization, the data is secured via encryption. The information is available in a hashed form that doesn’t allow anyone to decrypt it and get the original input.
Image source: Money
Traditional databases have centralization issues. One can steal the documents or hack the servers and get all the info at once. This problem is addressed by blockchain where data is encrypted and distributed. So hacking one or even several of the nodes cannot affect the overall network.
Renunciation of the middlemen has made blockchain a disruptive technology that proved to be robust for many industries from finance to supply chains, medicare, and many more. The years after the Bitcoin launch have proved versatility and trustworthiness of the blockchain technology which in turn confirms the effectiveness of hashing as a protection measure.
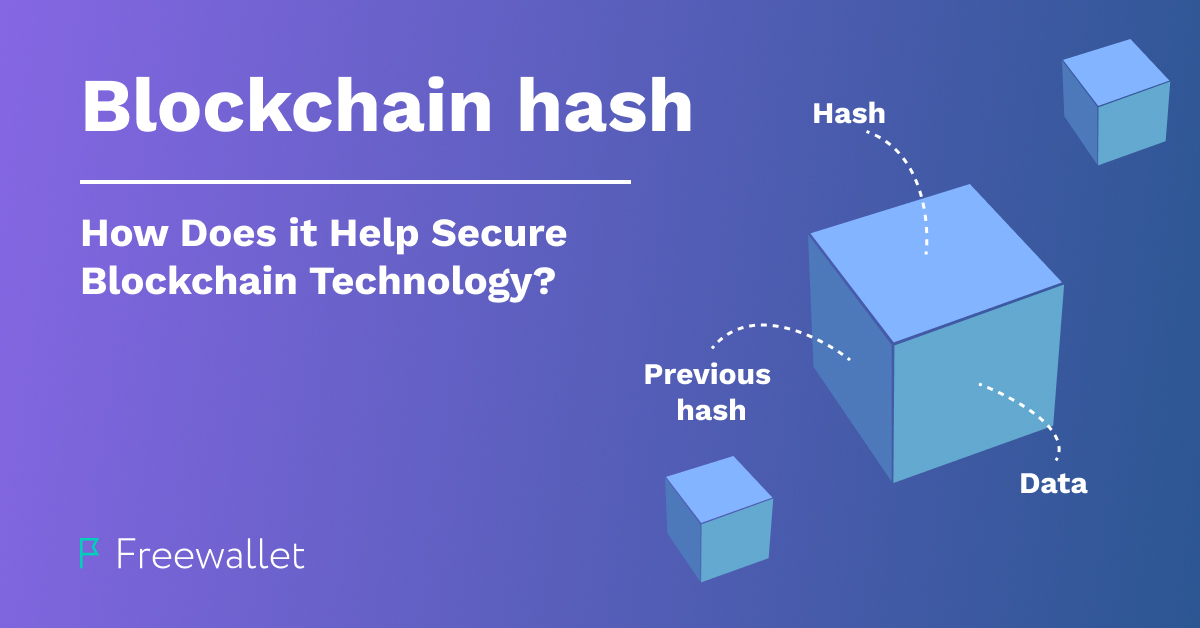
The data on blockchains are stored in “blocks” of transactions. Each block consists of data about a specific number of transactions. Once the needed amount is there, the block is created. The data related to the block is encrypted. The output looks like a hexadecimal number which is called hash. Then, the hash gets encrypted within the rest of the data on the blockchain and gets incorporated into the chain of all blocks.
Hashing in Blockchain Security
Pairs of keys (public and private keys) from crypto wallets, transaction IDs, and any other data you can think of is being hashed when it enters the blockchain. Although hashes are designed so that they cannot be used to retrieve the info that was encrypted, they are used to locate the needed data and verify it’s true. For instance, crypto wallets use hashes to confirm that the specific amount of the cryptocurrency in question was sent to a particular wallet address at the particular moment. In other words, the wallets can read the transaction info. If the blockchain is transparent (i.e., like the Bitcoin blockchain), we can check the transaction ourselves as blockchain explorers contain the timestamps, the amounts of crypto, and the addresses involved in the transaction. However, if we cannot find the info about the owners of these addresses anywhere, the transaction data will stay anonymous for us.
The inability to decrypt hashes makes blockchains so safe and effective. No one can tamper with the on-chain data. That’s the benefit of decentralization of public blockchains. The need to change a fragment in the blockchain data will require rewriting all the data in the subsequent blocks as each block contains the hashed data from all the previous blocks. This task is very demanding (not impossible though, especially for blockchains with a small number of nodes). The system won’t accept the altered block as the following blocks will contain conflicting data. Generally, such a design makes blockchains very safe and hashing plays a crucial role in protection of information stored in distributed ledgers.
Image source: Bitpanda
However, there are concerns about the low level of decentralization of some blockchains. If most hashing power is concentrated in the hands of only a few actors, they may collude to validate fraud transactions and tamper the blockchain data. To do so, the fraudsters should control over 50% of the hashing power. Hence the name of such a threat — 51% attack. Yet, the most popular networks have been avoiding these attacks. To perform such an attack, fraudsters must have a huge share in the hashing power of a specific cryptocurrency. But if they have it, they already can enjoy many benefits and profit from block validation. That is what keeps them away from criminal activity.
The Role of Mining
The first blockchain, Bitcoin, still utilizes a consensus mechanism, known as Proof-of-work (PoW) for the transactions validation. This procedure also involves hashing. To add a new block of transaction nodes that perform mining, a process of validating transactions, should solve a math puzzle of high difficulty. The solution has a form of hash. The first node to find the correct hash gets the block reward. That’s how “miners” (people who use their hardware to crack these puzzles) get paid for their job of validating transactions and keeping the entire network alive. The puzzles’ difficulty is dynamic. It reacts to the overall hashing power used for mining so that the new block is added once in the same period of time.
Most modern blockchains use other consensus mechanisms as Proof-of-work proved to be too harmful for the environment as it requires tremendous energy consumption. However, it doesn’t mean that other consensus mechanisms don’t rely on hash functions.
Common Hashing Algorithms in Blockchain
Different blockchains use different hashing algorithms. They have the same purpose — protecting the on-chain data.
SHA-256
The algorithm used in Bitcoin and Ethereum is known as SHA-256. The name stands for Secure Hash Algorithm 256-bit. SHA-256 is the successor of SHA-1.
Image source: ResearchGate
SHA-256 was coined by the US National Security Agency in 2002. SHA-256 applies a pretty simple encryption round, repeated 64 times. The alleged Bitcoin creator Satoshi Nakamoto could resort to using SHA-256 as this algorithm has a solid reputation while being not too complex.
Scrypt
Another common hashing algorithm is Scrypt. It was created in 2009 as a function for derivation of a password-based key. Soon, it was used for validation of Litecoin transactions. Another big cryptocurrency using Scrypt is Dogecoin.
As Scrypt was thought of as an algorithm preventing hardware spam attacks, it naturally became a strong ally for cryptocurrencies. More than that, initially, Scrypt was considered as an anti-ASIC algorithm. Nevertheless, ASIC producers found a way to modify their devices for LTC mining.
CryptoNight
This algorithm was created directly as a Proof-of-work element. CryptoNight was developed in response to the inability to continue mining BTC via the regular CPU devices. CryptoNight allowed CPU owners to mine cryptocurrencies on a relatively large scale. The most notable cryptocurrency using CryptoNight is Monero (XRM), a private-focused cryptocurrency.
Ethash
Ethash was developed to make Ether ASIC-resistant. It used an architecture similar to Scrypt but it required more memory to make mining via ASIC more or less worthless. Ethash is still used for the Ethereum Classic (ETC) mining. It is possible to mine this coin using GPUs. Ethash is not used outside the Ethereum mining.
X11
X11 is a complex algorithm comprised of 11 different algorithms combined into the whole. Just like the rest mentioned algorithms, it was coined for the PoW-based cryptocurrencies. X11 consumes less energy than most algorithms used in the PoW-based cryptos. The most known cryptocurrency using X11 is Dash.
Conclusion
Now you can see how hashing is crucial for blockchain. It serves for the operations, for verifying the exact pieces of data, and for protection of all the information on blockchain, including your money. Various hashing algorithms are developed and applied. The best of them can compete in levels of efficiency, however most of them are pretty trustworthy.
Related
Stay tuned
Subscribe for weekly updates from our blog. Promise you will not get emails any more often.
Most Popular
New Posts
Stay tuned
Subscribe for weekly updates from our blog. Promise you will not get emails any more often.